创建Git仓库用于存放Terraform代码
创建.gitignore
1 | # ignore local .terraform dir |
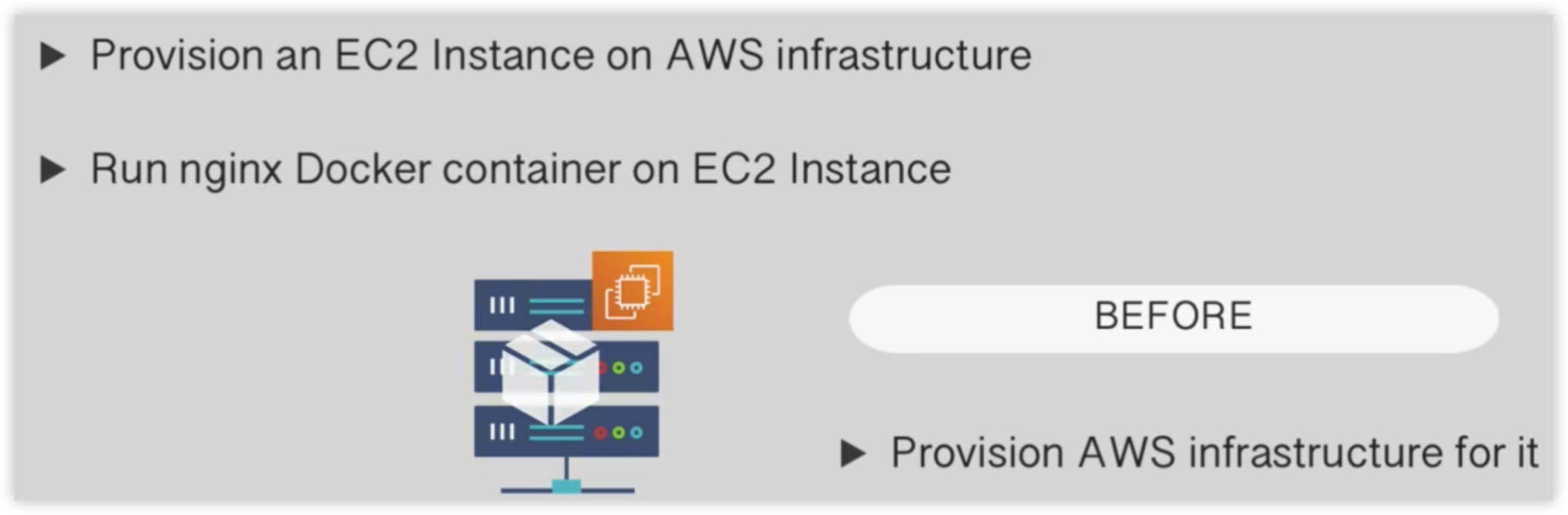
目标:创建一个EC2实例,并且在EC2里运行一个nginx docker容器
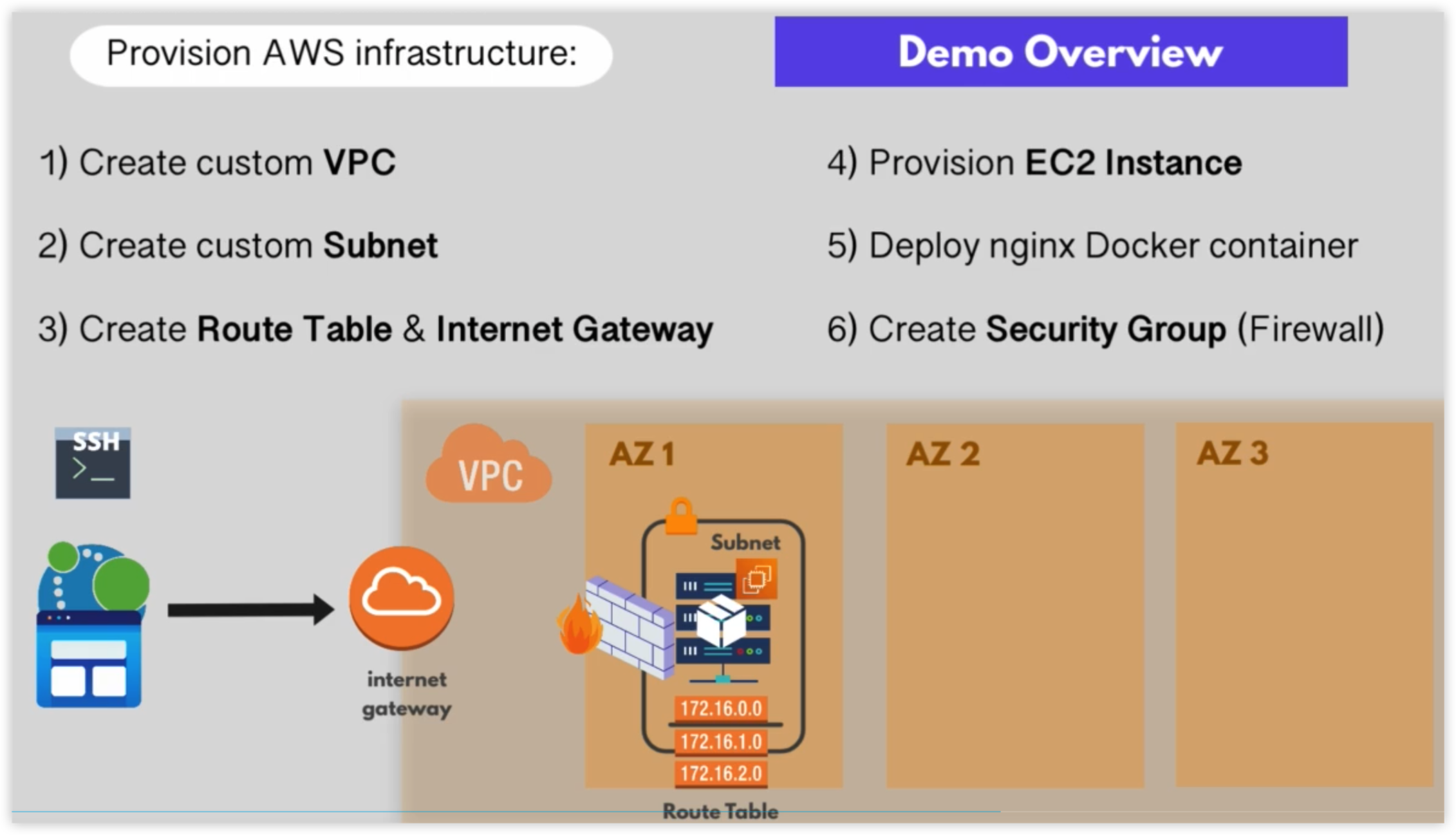
需要创建的AWS资源
*最好不要使用默认的AWS资源
- 创建VPC
- 创建Subnet
- 创建Route Table & Internet Gateway
- 创建EC2
- 部署nginx docker容器
- 创建Security Group(Firewall),并允许ssh
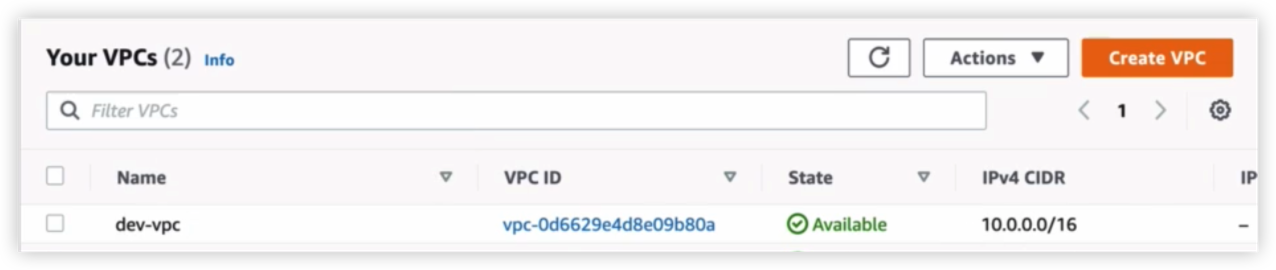
创建VPC & Subnet
terraform.tfvars
1 | vpc_cidr_block = "10.0.0.0/16" |
main.tf
1 | provider "aws" { |
在AWS上查看结果
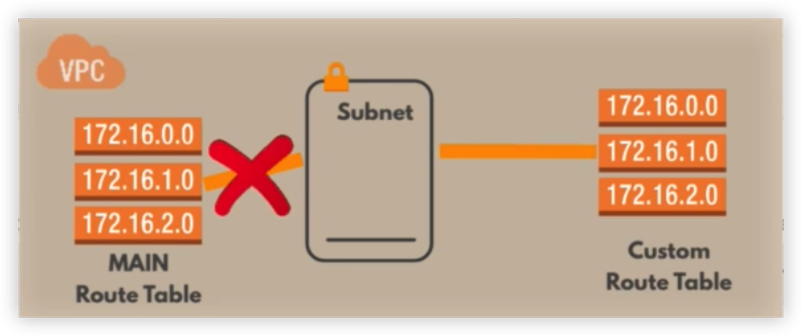
Route Table
Route table决定了VPC转发的目的地
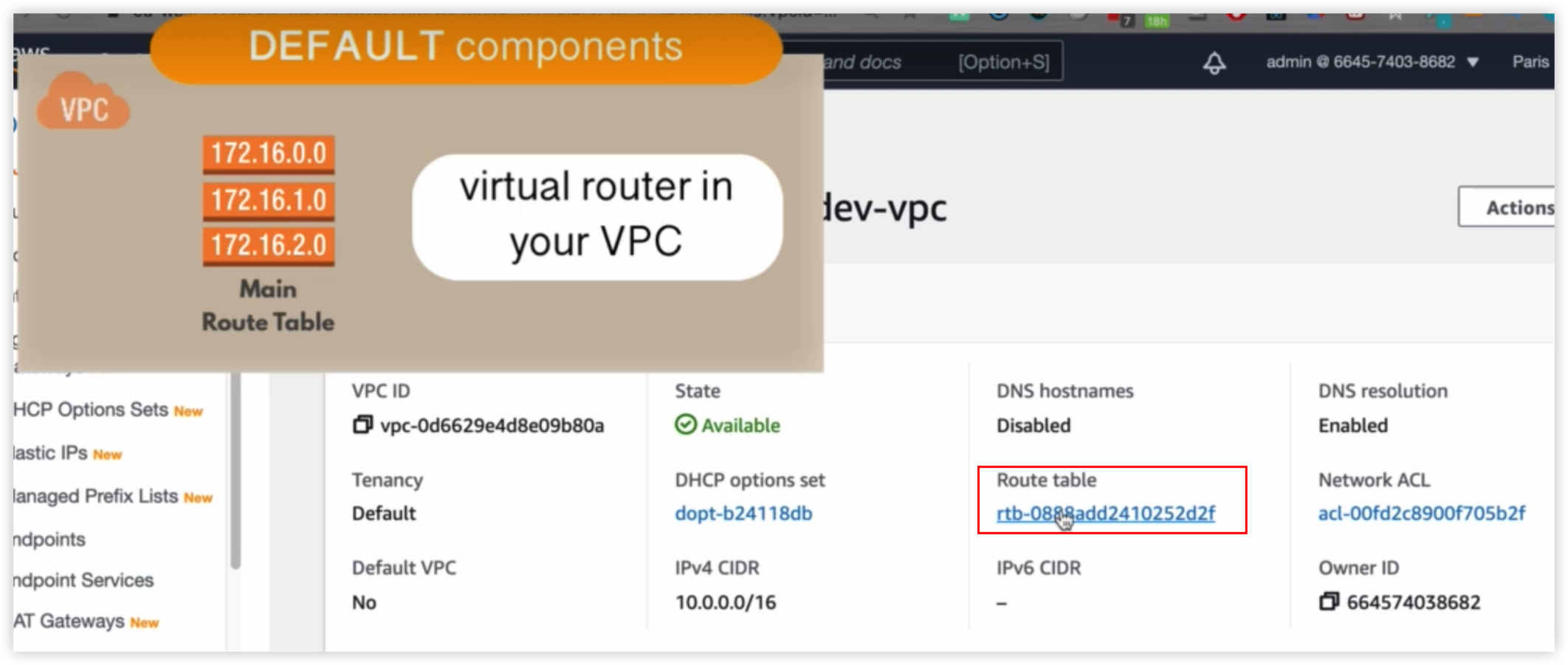
在Terraform code不必根据执行的先后来编写代码
1 | # 创建Route table |
执行结果
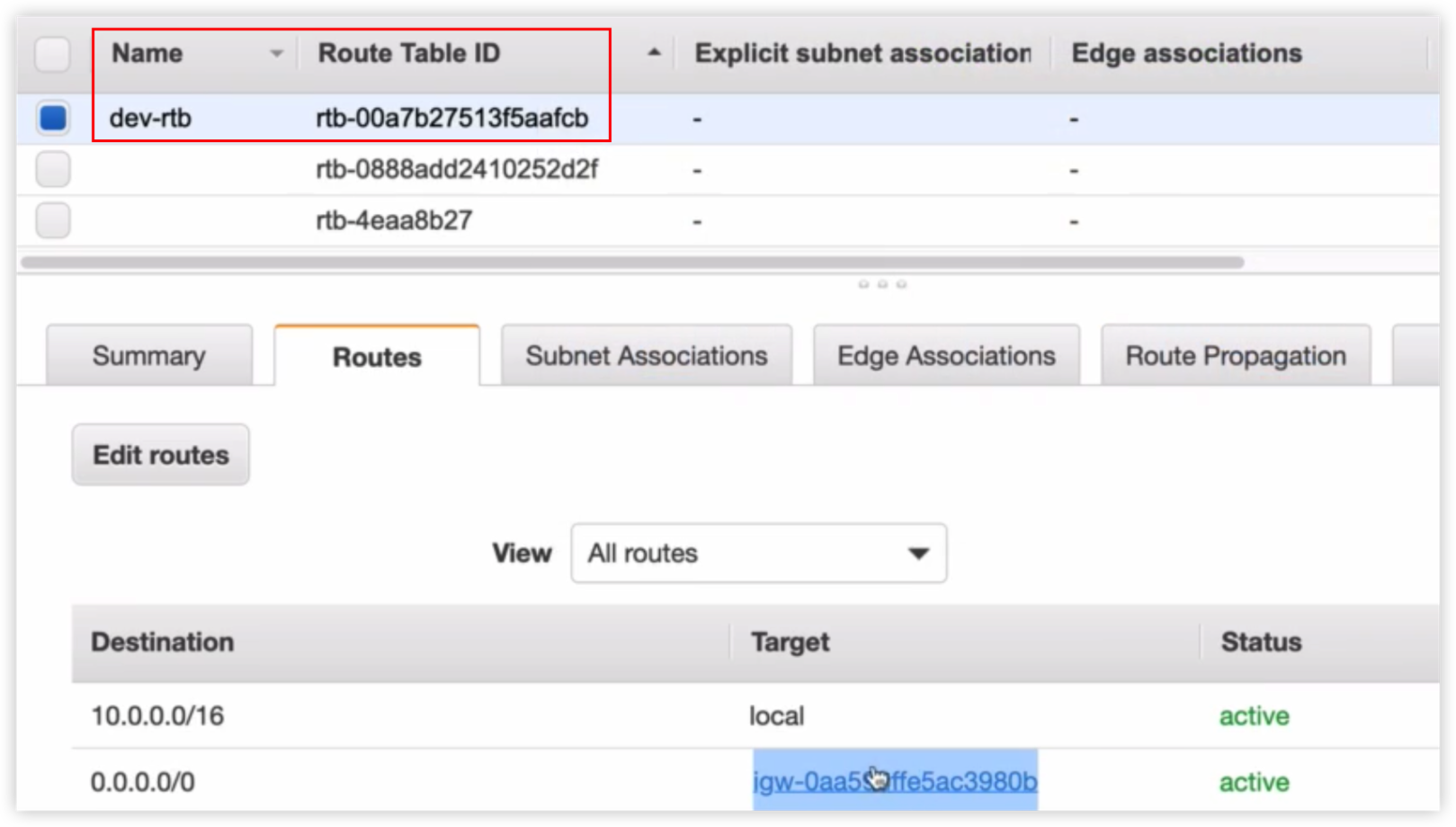
同时还要为Route table和Subnet创建关联
Terraform code
1 | # Route table & Subnect |
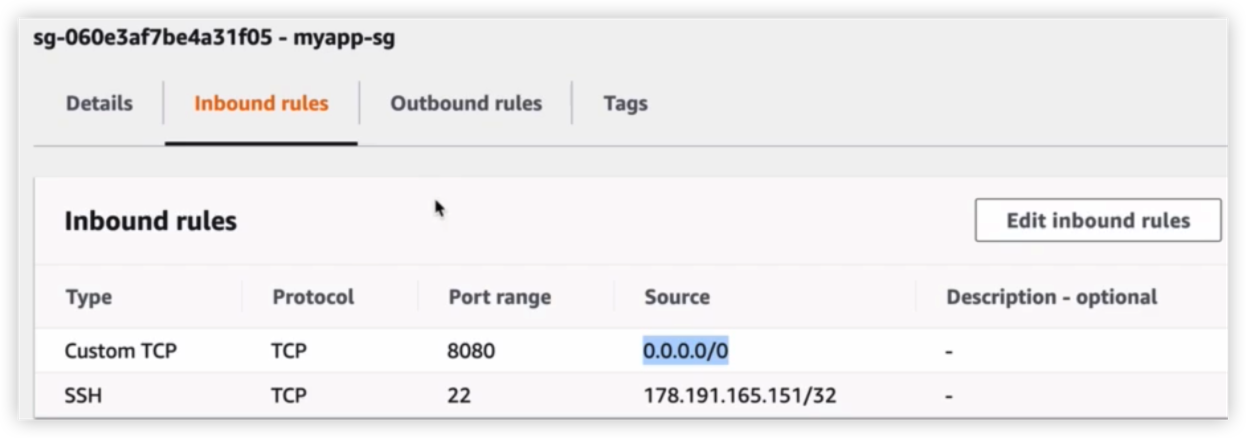
Security Group & Firewall
创建安全组
Terraform code
1 | # Security Group |
执行结果
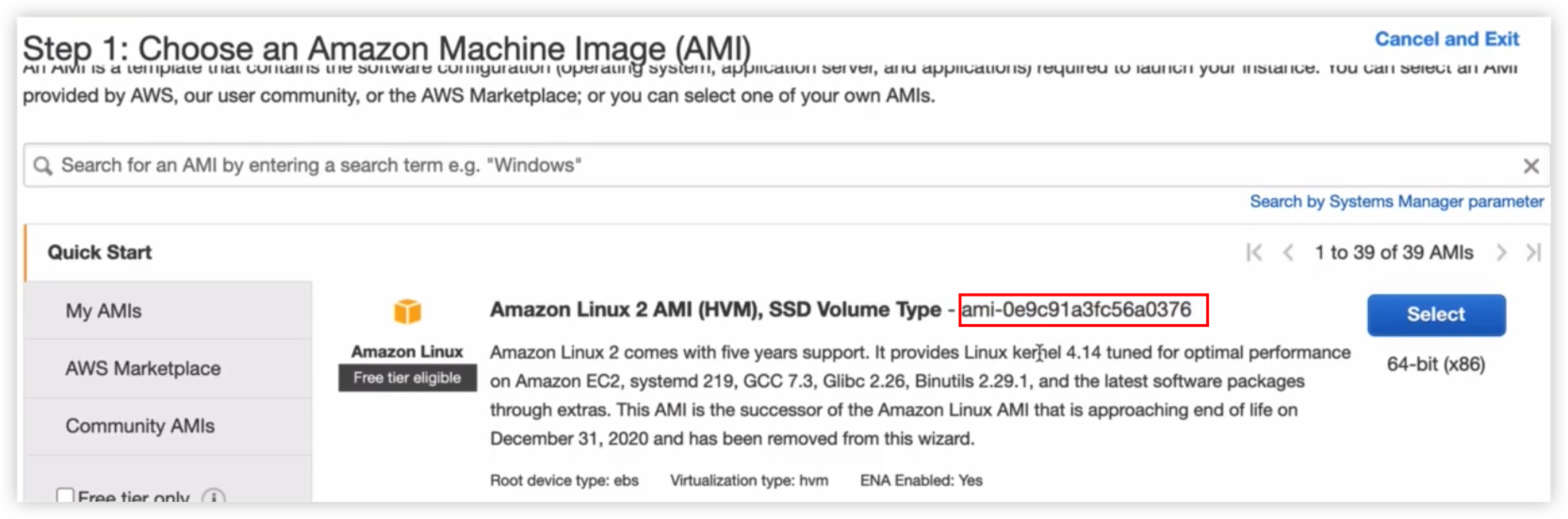
EC2 & AMI
Amazon Machine Image(AMI)是aws提供的操作系统镜像,用户可以根据AMI创建自己的操作系统实例。
Terraform code
1 | # AWS AMI data definition |
等待EC2创建

EC2 initialize script
添加 user_data=,设置EC2初始化时自动运行脚本
下图中的代码块只会在初始化的时候被执行一次
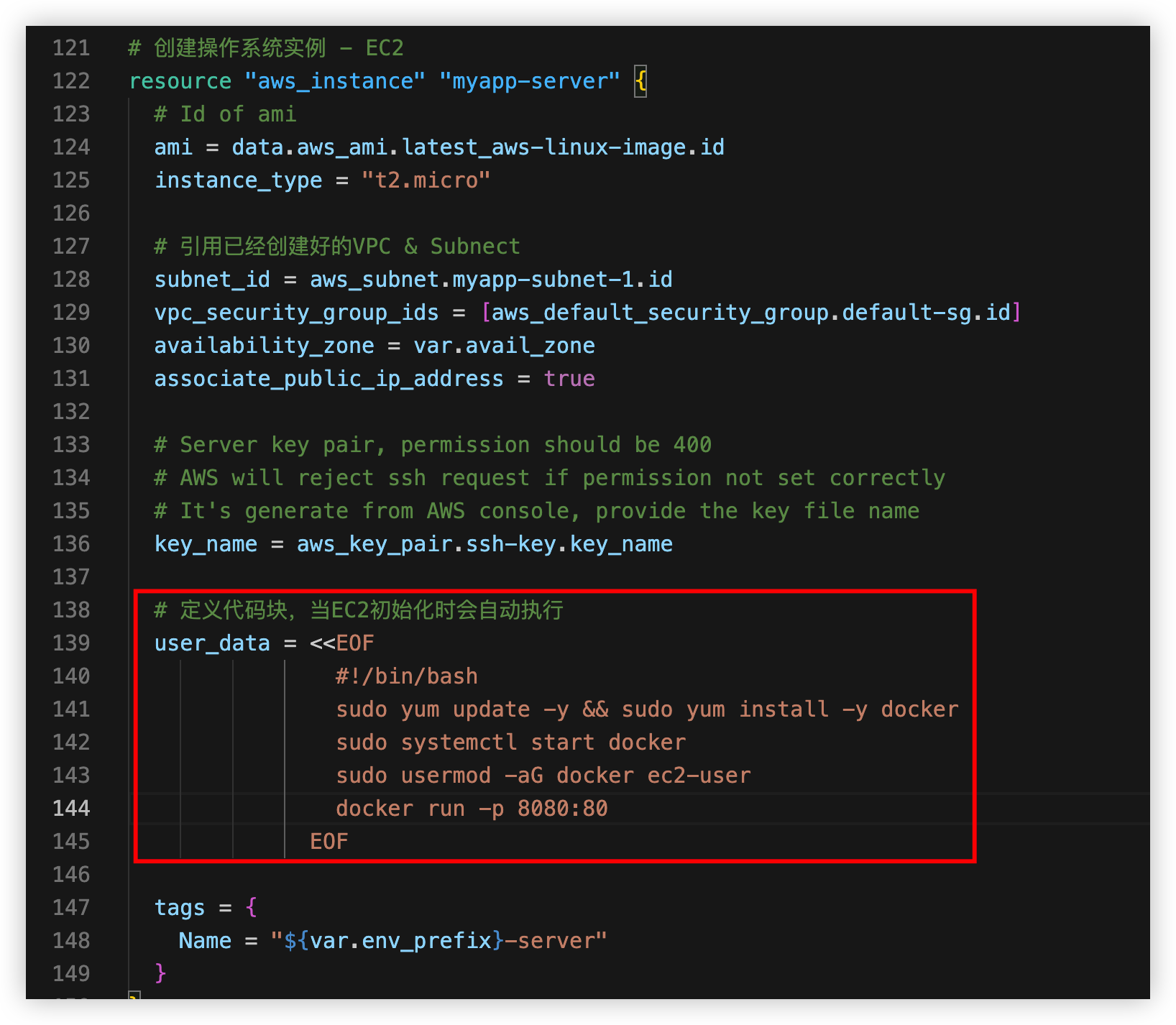
如果需要执行定义好的脚本而不是代码块,可以使用如下方式

另一种方式:使用Provisioner执行脚本
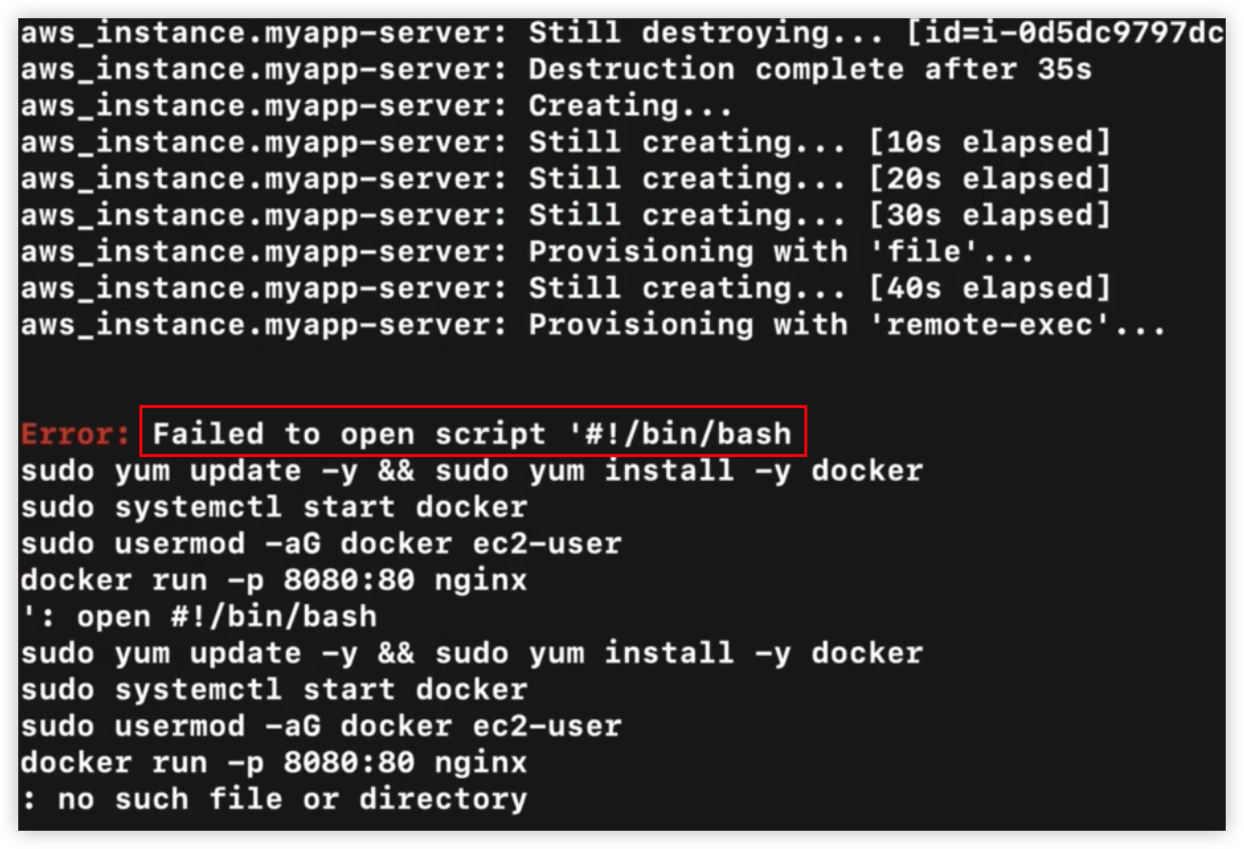
使用remote-exec在EC2上执行脚本
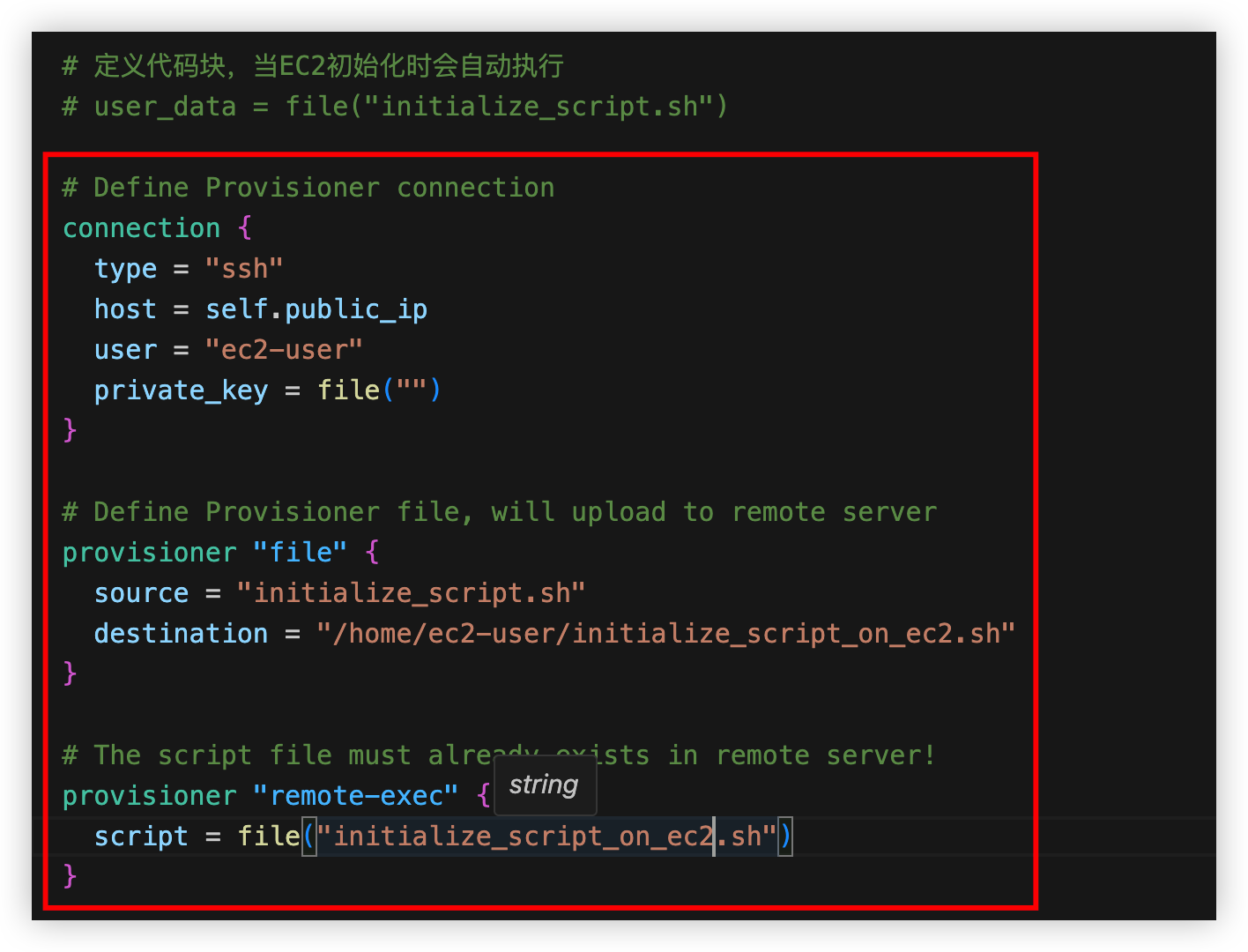
可以使用local-exec在本地机器上执行命令
1 |
|
Terraform文档上说明Provisioners是没有其他选择时的最后手段
- 尽量采用
user_data而不是Provisioners - 尽量使用”local provider”取代
local-exec - 尽量采用配置管理工具取代
Provisioners,如Ansible, Jenkins
实际上Provisioners打破了Terraform的概念。Terraform能通过相同的组件状态总是提供一致的返回结果,但是Provisioners执行的脚本却是未知的,Terraform无法获取到其中的状态。

一种可能的情况是,Provisioner中的脚本执行错误,此时terraform不会返回具体的状态信息。
这种状态下无法得知EC2具体是否被创建